Phishing attempts continue to rise as they are one of the easiest methods for cybercriminals to gain access to valuable information. Three recent phishing attacks include:
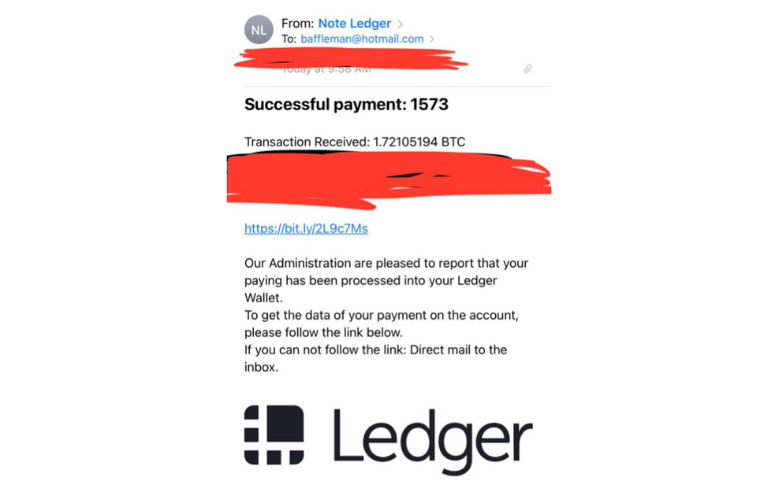
Ledger Wallet
Ledger is a cryptocurrency wallet that was targeted by a phishing email that looked authentically to be coming from Ledger support that falsely alerted users that their Ledger assets had been compromised and were infected with malware. The email looked very official but on close inspection when CoinDesk independently reviewed one of the phishing emails, which was sent from “support@legder.com” they saw that it was a slight misspelling of the real address “ledger.com”. Ledger has reported that they discovered it and patched it and that all customer data was safe, but users are still receiving phishing emails and it appears from an earlier breach that hackers gained access to the marketing database.
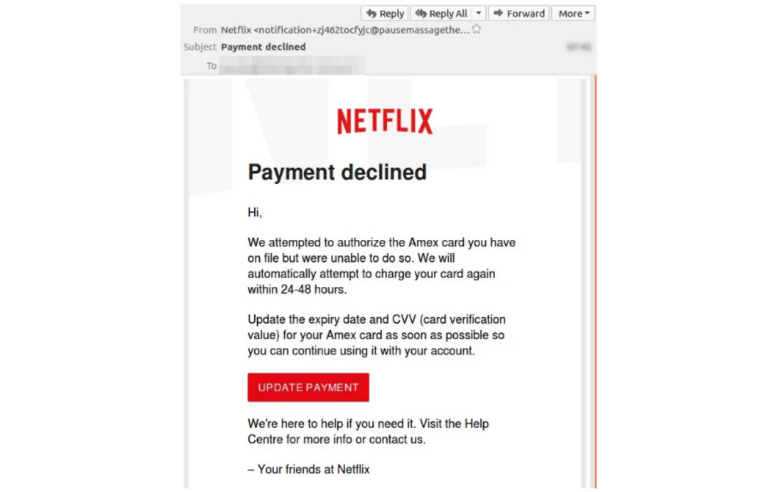
Netflix Phishing
As more people stayed home and were watching streaming services, Netflix was targeted with a phishing scam claiming there was a problem with billing and account information had to be verified or the service would be shut off. The link in the email actually bypassed many security controls by using a CAPTCHA page with Netflix logos that directed to a fake page to gather the information that then rerouted to the actual Netflix page.
1. URLs
Always check the URLs in the email and filter them against threat intelligent data sources to see if they are legitimate or not.
Unfortunately, everyone is at risk of phishing attacks. When you investigate phishing emails, DTonomy suggests the following:
2. Attachments
Hackers use attachments to deliver malware or embed malicious URLs in attached documents. Run them through a sandbox or check the file hash against threat intelligence to make sure they are legitimate and that the links in the attachment are legitimate as well.
3. Sender IP
Check if the Sender IP has been flagged as spam in a public data source such as AbuseIPDB.
4. DMARC/SPF/DKIM
DMARC/SPF/DKIM are protocols to protect spammers and phishers from spoofing your domain. In the header of your authentication results from incoming email, check the DMARC/SPF/DKIM syntax for pass or fail results.
5. Sender Verification
Check if the sender’s name or a subset of the sender’s name matches the email domain. Also, check if the sender’s email was compromised before using threat intelligence or the sender is legitimate. Analyze the sender’s domain to see if this domain was blocked or reported as a scam domain.
6. Sentiment
If everything else is legitimate, the email could be coming from a hacked email box. Check the sentiment of the email. Does it introduce a sense of urgency or introduce fear of losing access or stimulate financial interests?
DTonomy offers simple plugins for Outlook and Gmail to provide assistance in evaluating phishing emails. The professional version has more advanced techniques integrated enabling you to investigate hundreds of suspected phishing emails quickly.
Social engineering and phishing account for 70% to 90% of MALICIOUS breaches. DTonomy can help you to respond to this weakest link as quickly as possible to avoid any severe data loss.
When you are ready, here are four ways we can help
- Schedule a free consultation to discover the best anti-phishing solutions for you and your team (schedule here)
- Leverage free phishing plugins to analyze your suspected email in outlook and Gmail (Outlook, Gmail)
- DTonomy’s AIR platform enables security teams to automate security analysis and response with AI-based scoring. It takes less than 20 minutes to get everything set up. Get started today! (Sign up here)
- Let DTonomy set up affordable phishing awareness training and manage phishing threats for you by requesting professional service here