Among the many new challenges that the COVID-19 pandemic has brought to security analysts, a recent and very serious one is unemployment benefits fraud. Criminals are filing claims for benefits using the credentials of people who haven’t lost their job. They learn of it when they get a letter from the government about the status of their claims or when the Department of Unemployment calls the individual to verify their identity. In Massachusetts alone, a national crime syndicate used stolen identities to try to steal $158M from the state’s unemployment fund.
Higher Education Institutions are No Exception
This recent phenomenon has added even more stress and workload to already busy analysts and increased risk to all businesses including higher education.
Universities tend to be challenging environments in which to manage cybersecurity threats with many multiple endpoints that are not owned by the institution and an ever-changing population of students, professors, and employees who access the internal systems.
One university learned of the Unemployment fraud when the Human Resources department was notified by the State Department to determine if an employee who filed for claims was actually unemployed. Apparently, employees’ credentials were being shared on the dark web and criminals were then filing unemployment claims on their behalf.
Automation with DTonomy AIR
The university noticed that many of the unemployment claims were fraudulent. The security analysts were immediately notified to investigate if data was being leaked internally and began running queries against internal systems to identify abnormal logins from unusual locations.
DTonomy AIR can augment the analyst’s work by providing a workflow that performs an automated broader analysis of anomalous logging to their internal network and take pre-approved actions accordingly, saving a significant amount of time on the part of the analysts.
When HR learns of a fraudulent claim, they send an email alert to the security analysts with the relevant information. The workflow built on the DTonomy AIR platform:
- automatically parses the email and extracts users mentioned in the email
- cross correlates their activities in the SIEM
- confirms with each user selective login history and decides if additional remediation steps need to be taken
The comprehensive workflow is here:
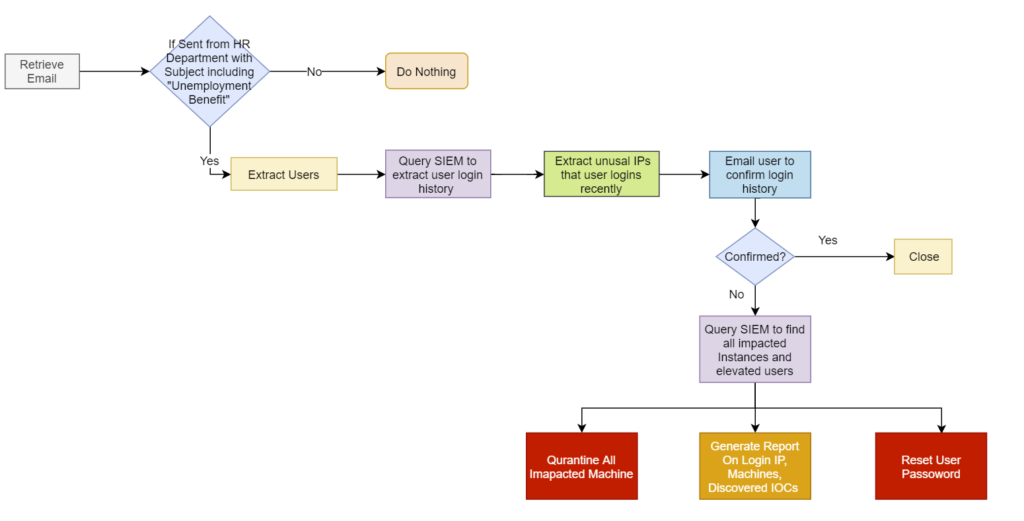
Using automation, DTonomy AIR helps analysts handle hundreds of reported users that may be impacted by this type of fraud and saved 95% of the time manually triaging each individual user. This workflow can also be applied to triage other types of fraud such as purchase order fraud, another nationwide fraud scam that is targeting suppliers at colleges across the country.
Additional Resources:
Sign up here for DTonomy AIR freemium edition.