Office 365, one of largest SaaS platforms used by organizations, is constantly on the radar of malicious hackers. Companies store volumes of mission critical and sensitive data on the platform, which they assume is protected and secure.
A recent report found that 25% of phishing attacks are able to circumvent Microsoft 365 security. The more common ways that hackers may gain access to Office 365 (Share Point, One Drive, Exchange, Teams, Skype etc.) environments are through phishing, stealing credentials from users, installing malware, auto-forwarding phishing emails to others, and leaking sensitive data.
Some specific examples of Office 365 related phishing that our clients have seen include:
- An email that looked like a password reset link, but had a big “click here if you did not request this reset to secure your account” button, encouraging the user to click on it
- A hacker calling an executive impersonating the “IT Staff” and asking them for their credentials to help stop an attack or some other malicious activity
- A phishing email with the organization’s actual logo on it to make it look official, the more authentic an email looks, the more likely a user may click on a bad link
How to Defend against These Office 365 Attacks?
Security analysts must make sure that all settings are configured correctly and must proactively review Office 365 login history to conduct proactive detection as well as rely on employees to report a suspected account compromise or phishing email.
A few typical detections could be
- Failed login on attempts
- Geographically impossible access
- Account use after termination
DTonomy Guided Investigation and Response
Not every alert is a true positive, therefore, careful investigation is needed. Take phishing as an example:
Investigation
You may want to conduct further investigation to:
- Analyze the header to see if it is coming from an unwanted location or known ad campaign
- Analyze URLs using external threat intelligence
- Analyze attachments with a sandbox to see if there is malware beaconing to external addresses
- Correlate with other internal information
Decision
Based on the information, you will need to make decisions as to how to proceed:
- If any entity is malicious, it should be marked malicious
- If nothing is found to be abnormal, it should be marked as benign
Response On false positives,
- Take notes and send email to those who reported
Response On true positives,
- Enable 2 FA on this user
- Block the URL
- Find users that have received the same email
- Etc.
The unique part of DTonomy is that we take your system setting and knowledge into consideration to make personalized recommendations for your environment. Automation can then be achieved through built in playbooks. Typically, these tools below are utilized in addition to DTonomy:

Based on recommendation, the automated playbook for this scenario could be like:
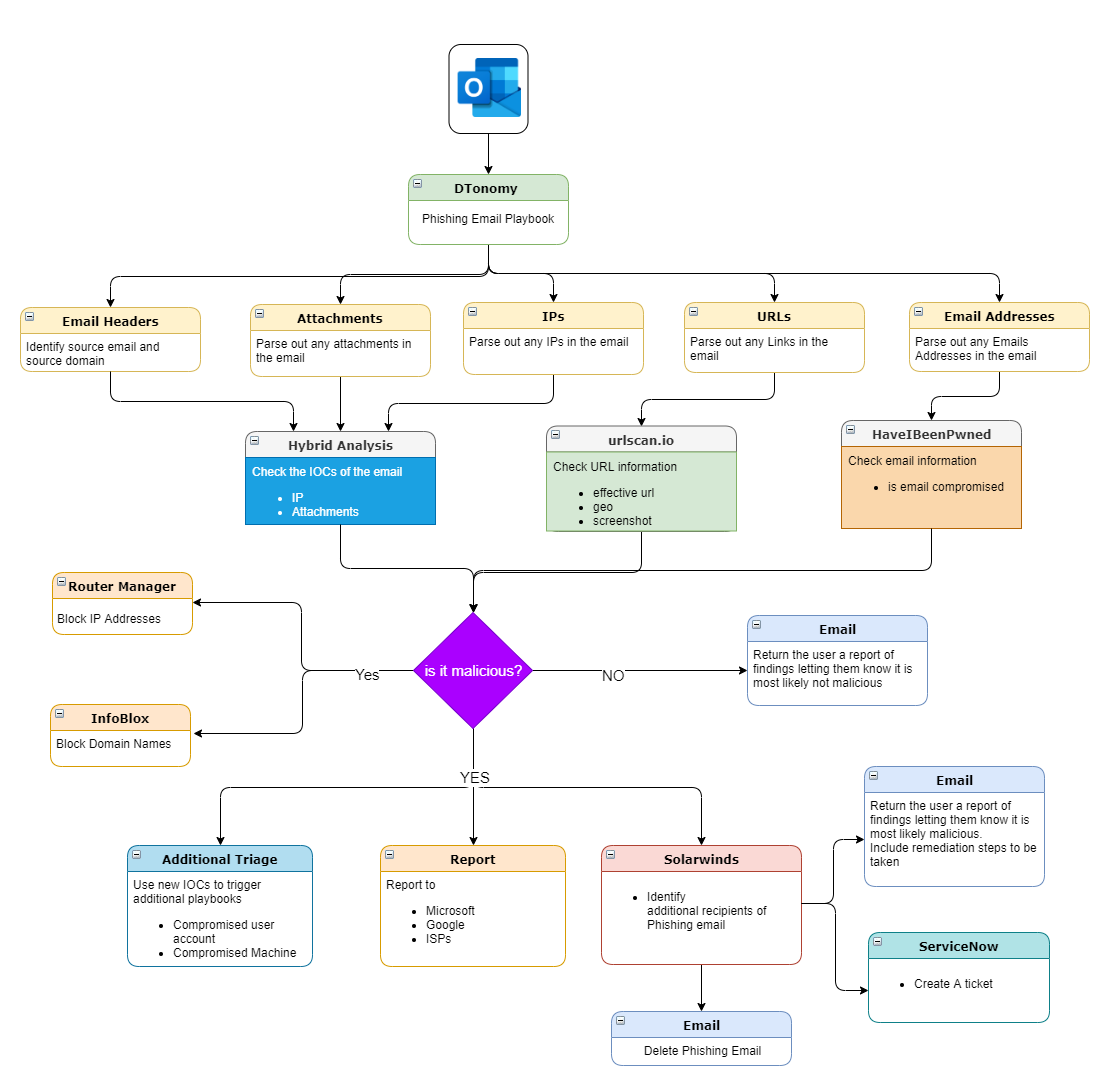
Only DTonomy uniquely learns a wide variety of security response workflows and recommends the best suitable decision and actions to guide you in your response and automates them to help you further secure your data on Office 365.
Want to learn more about DTonomy? Schedule a demo