What is the “SolarWinds Hack?”
SolarWinds is a network performance and systems monitoring software company. SolarWinds Orion is their software product for network security monitoring which enables centralized monitoring and management of an entire IT stack from infrastructure to applications deployed on premises, in virtualized environments or in Microsoft Azure. In early December, FireEye, a cybersecurity company focused on the detection and prevention of cyber-attacks, discovered that they had been hacked via the SolarWinds Orion platform, and also that the threat actors stole Red Team assessment tools that FireEye uses to probe its customers’ security. The hackers, assumed to be a foreign nation-state, had gained access as early as October 2019 via trojanized updates to the Orion IT monitoring and management software and had gone undetected since then.
How was the SolarWinds attack discovered?
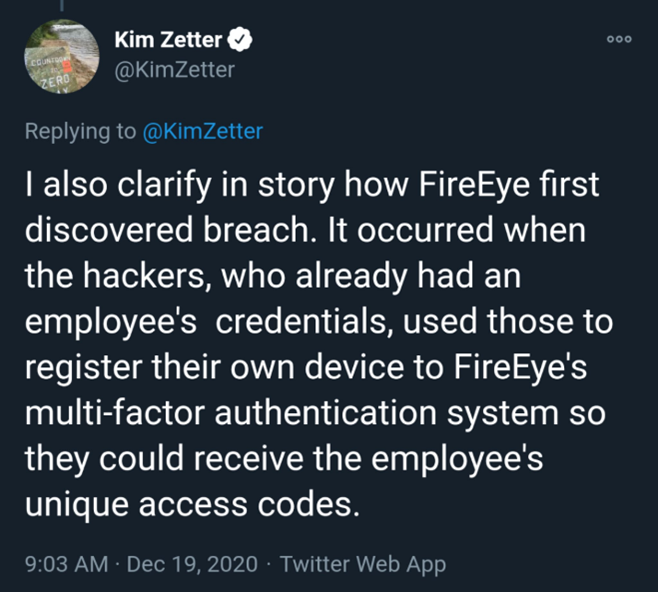
From what we can conclude so far, FireEye discovered that they had been breached by noticing a new device that had registered to FireEye’s multi-factor authentication system. A Twitter post by Kim Zetter, an American investigative journalist and author who has covered cybersecurity and national security since 1999, exposed that the hackers had obtained an employee’s credentials and were registering their own device in an attempt to get the employee’s unique access codes.
What is the impact of the attack?
As one of the biggest cyber-attacks, the implications of this breach are far-reaching. 18,000+ customers of SolarWinds are believed to have been exposed through compromised updates, including many major U.S. government agencies, but also many high-tech companies including Cisco, Intel, Microsoft, VMWare and Belkin, corporations, hospitals, and universities across North America, Europe, Asia and the Middle East.
SolarWinds claims that its customers include most of America’s Fortune 500 companies, the top U.S. telecommunications providers, all five branches of the military, the State Department, the National Security Agency (NSA), and the Office of the President of the United States.
How was the attack executed?
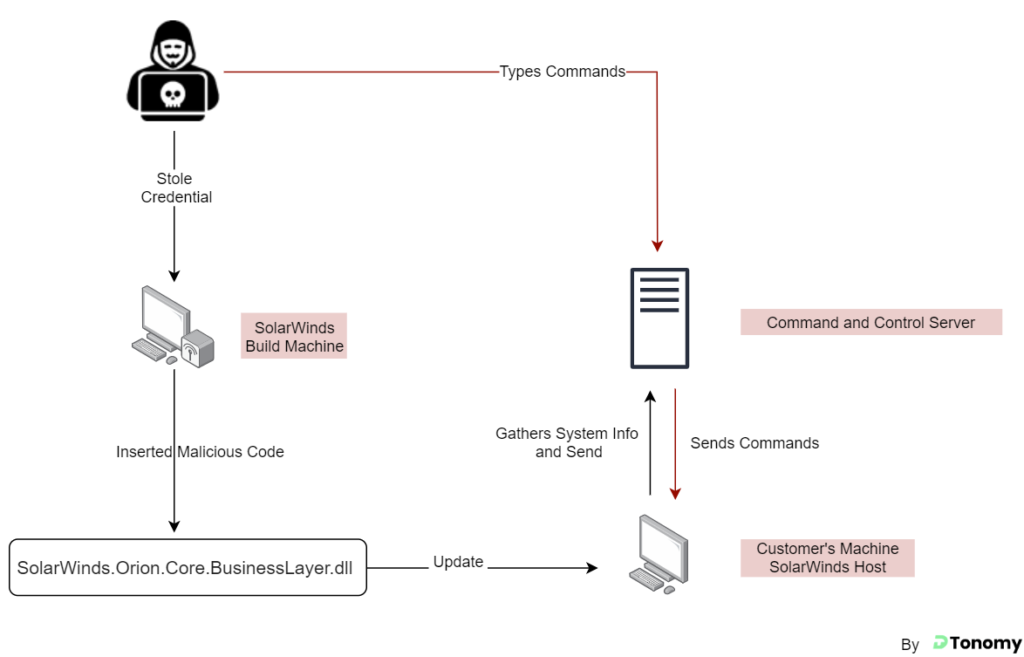
The attackers gained access to the SolarWinds Orion build system and added a backdoor to the legitimate SolarWinds.Orion.Core.BusinessLayer.dll DLL file. This DLL was then distributed to SolarWinds customers in a supply chain attack via an automatic update platform used to push out new software updates. Once installed, this backdoor then connects back to the remote command and control server to receive jobs or tasks to execute on the infected server. These types of commands allow the hackers to read and write files, initiate processes, and upload information to their servers.
If you suspect you have been affected, what should you do now to remediate?
SolarWinds has released a Security Advisory here. Given that the attack is likely ongoing, and the extent of the attack is still not completely understood, if you use SolarWinds anywhere in your environment, it may be best to assume that you may have been breached and take some cautionary steps.
- Isolate the SolarWinds server for further investigation
- Change the passwords for all accounts that have access to SolarWinds infrastructure
- Add IOCs to your monitoring list
What can you do to better detect and prevent such breaches in the future?
Given that it is believed that the hackers had infiltrated SolarWinds systems since at least last spring, they had nine months of malicious behavior before they were first detected. Once inside, hackers often conduct unusual behaviors such as lateral movement, beaconing, adding temporary files, modifying tasks temporarily, etc. which should generate alerts to security teams. These alerts are not always noticed or properly addressed as sophisticated hackers often leak weak signals which are usually considered as noise by analysts. As noted by the following, an overload of alerts creates a big challenge on how to handle them.
Many security teams have decided to turn off 90% of their alerts and only focus on the easier ones or the top priorities and leave the rest uninvestigated. At DTonomy, we completely understand the frustration of alert fatigue and overload, but we also believe that any alert that is not addressed is a significant risk to the company. Hence, we developed DTonomy AIR to combat alert fatigue and assure that stealth signals are not neglected within your environment by leveraging intelligence and automation.
Supply chain compromise continues to be a growing concern in the security industry. The SolarWinds incident is a grave reminder that these kinds of attacks can achieve the harmful combination of widespread impact and deep consequences for successfully compromised networks. As part of the cyber security community, DTonomy will continue to help make the world a better and secure place.
Never forget why you started, and you can accomplish your mission.